The CyLab program is fueled by the support of corporations and government agencies looking for both the vital research that delivers answers to difficult questions and the probing minds that articulate those answers.
Every week, during the school year, the CyLab Seminar Series provides updates on the latest research by our faculty, as well as by visiting scholars from other prestigious institutions.
Access to our weekly webcasts and on-line archive of Cylab Seminar Series is one of the exclusive benefits of membership in the CyLab's private sector consortium.
From time to time, CyLab offers rare glimpses into its Seminar Series with the release of select videos via both the CyLab You Tube Channel and CyLab at iTunesU.
On February 20th, 2012, the CyLab Seminar featured CyLab Research Systems Scientist Jonathan McCune on Verifying the Integrity of Peripherals' Firmware on SensorFly and Beyond: Flying Sensing Systems in the Wild.
Friday, March 23, 2012
CyLab Seminar Series: Pei Zhang on SensorFly and Beyond: Flying Sensing Systems in the Wild
The CyLab program is fueled by the support of corporations and government agencies looking for both the vital research that delivers answers to difficult questions and the probing minds that articulate those answers.
Every week, during the school year, the CyLab Seminar Series provides updates on the latest research by our faculty, as well as by visiting scholars from other prestigious institutions.
Access to our weekly webcasts and on-line archive of Cylab Seminar Series is one of the exclusive benefits of membership in the CyLab's private sector consortium.
From time to time, CyLab offers rare glimpses into its Seminar Series with the release of select videos via both the CyLab You Tube Channel and CyLab at iTunesU.
On February 6th, 2012, the CyLab Seminar featured CyLab researcher Pei Zhang on SensorFly and Beyond: Flying Sensing Systems in the Wild.
Every week, during the school year, the CyLab Seminar Series provides updates on the latest research by our faculty, as well as by visiting scholars from other prestigious institutions.
Access to our weekly webcasts and on-line archive of Cylab Seminar Series is one of the exclusive benefits of membership in the CyLab's private sector consortium.
From time to time, CyLab offers rare glimpses into its Seminar Series with the release of select videos via both the CyLab You Tube Channel and CyLab at iTunesU.
On February 6th, 2012, the CyLab Seminar featured CyLab researcher Pei Zhang on SensorFly and Beyond: Flying Sensing Systems in the Wild.
CyLab Seminar Series/Business Risks Forum: Mike Susong on Application Of Intelligence Principles To Raise IT Security To The Next Level
The CyLab program is fueled by the support of corporations and government agencies looking for both the vital research that delivers answers to difficult questions and the probing minds that articulate those answers.
Every week, during the school year, the CyLab Seminar Series provides updates on the latest research by our faculty, as well as fby visiting scholars from other prestigious institutions. In addition to these academic research presentations, occasional Business Risks Forum events feature security experts from business and government to deliver invaluable insights on the facts on the ground in the operational environment.
Access to our weekly webcasts and on-line archive of Cylab Seminar Series is one of the exclusive benefits of membership in the CyLab's private sector consortium.
From time to time, CyLab offers rare glimpses into its Seminar Series with the release of select videos via both the CyLab You Tube Channel and CyLab at iTunesU.
On February 27th, 2012, CyLab presented security intelligence expert Mike Susong in a CyLab Seminar Series Business Risks Forum event. Susong, co-founder of iSIGHT, spoke on Application Of Intelligence Principles To Raise IT Security To The Next Level.
Every week, during the school year, the CyLab Seminar Series provides updates on the latest research by our faculty, as well as fby visiting scholars from other prestigious institutions. In addition to these academic research presentations, occasional Business Risks Forum events feature security experts from business and government to deliver invaluable insights on the facts on the ground in the operational environment.
Access to our weekly webcasts and on-line archive of Cylab Seminar Series is one of the exclusive benefits of membership in the CyLab's private sector consortium.
From time to time, CyLab offers rare glimpses into its Seminar Series with the release of select videos via both the CyLab You Tube Channel and CyLab at iTunesU.
On February 27th, 2012, CyLab presented security intelligence expert Mike Susong in a CyLab Seminar Series Business Risks Forum event. Susong, co-founder of iSIGHT, spoke on Application Of Intelligence Principles To Raise IT Security To The Next Level.
Thursday, March 1, 2012
Notes on RSA 2012: Diffie, Rivest & Shamir Shine on Crypto Panel, Ranum, Too, re: Cyber War
RSA Conference 2012: An All-Male "Industry Experts" Track

Fortune-Teller at WhiteHat Security's Fantastic Party (OSHA Thai)

Notes on RSA 2012: Diffie, Rivest & Shamir Shine on Crypto Panel, Ranum, Too, re: Cyber War, Otherwise an Off Year
By Richard Power
There is nothing wrong with your television set. Do not attempt to adjust the picture. We are controlling transmission. If we wish to make it louder, we will bring up the volume. If we wish to make it softer, we will tune it to a whisper. We will control the horizontal. We will control the vertical. We can roll the image, make it flutter. We can change the focus to a soft blur or sharpen it to crystal clarity. For the next hour, sit quietly and we will control all that you see and hear. We repeat: there is nothing wrong with your television set. You are about to participate in a great adventure. You are about to experience the awe and mystery which reaches from the inner mind to — The Outer Limits. Opening narration, Outer Limits (circa 1960s)
Notes on RSA 2012: Diffie, Rivest & Shamir Shine on Crypto Panel, Ranum, Too, re: Cyber War
By Richard Power
Leap Year? End of the Mayan Calendar? "Owned" by Anonymous? An Off Year at RSA?
It was a strange year at the RSA Conference.
Maybe it was the repeated cries of "Hold on to your raffle tickets!" that rose above the din of the Expo floor. Maybe it was the Sumo wrestler in traditional garb, i.e.. a HUGE, nearly NAKED man, brought into the Expo hall to pose for photos with giddy little attendees.
Maybe it was the "Industry Experts" track. I counted twenty-nine speakers; some who are actually experts, and some who are not, but NO WOMEN. This is disturbing. (I can't understand why RSA's marketing mavens didn't object to this for appearances sake. How could they miss it? And if they proceeded with this glaring imbalance intentionally, it is even more disturbing). I do not find it disturbing on some basis of political correctness, I find it disturbing because cyber security is a VERY SERIOUS challenge to the future of our civilization, and because the most important element of this challenge is the HUMAN FACTOR, and because meeting this challenge successfully will require BOTH HALVES of the human psyche.
Maybe it's just that Anonymous has knocked the stuffing out of some serious players.
Maybe it was Leap Year. Maybe it was the end of the Mayan Calendar.
(BTW, the end of the Mayan Calendar is the obvious theme those RSA Conference marketing mavens should have seized on for this 2012 event. Instead, they choose "The Great Cipher is Mightier Than the Sword," accompanied by a very underwhelming graphic design. An unfortunate and unusual "fail" for the RSA Conference. Most years, the event's themes and graphic designs are quite powerful. The great cipher is mightier than the sword? Well, perhaps, but the pen is still mightier than both.)
Maybe it was just me.
This year, I choose not to attend the opening day keynotes, delivered by RSA Executive Chairman Art Coviello, Microsoft VP Scott Charney or Symantec CEO Enrique Salem, So no "control" had been imposed over "the horizontal and vertical" before I walked the Expo floor.
Maybe that's why for a moment or two, immediately after I crossed the threshold, I was overtaken by powerful flashback to two moments, one from the 1960s and one from the 1980s, which have now become unstuck in time.
Yes, this year's RSA Conference sounded like, smelled like and most resembled either the New York Colseum automobile show that an uncle took me to when I was a little boy, or the now defunct Comdex trade show (Las Vegas, circa 1980s). (Do you remember Comdex? )
So as I wandered up and down the aisles, first, I pondered the ways in which both the car show and the RSA exhibition hall sought to identify products with powerful archetypes in the psyche; at the car show, the not so subliminal message was if you buy this "Mustang" or this "Malibu" you would be more sexually powerful, at the RSA Expo, the not so subliminal message is if you buy this product you will be a 21st Century cyber warrior invulnerable to attack. And yes, the promise of "security" that envelopes the products displayed on the RSA Expo floor is often as vacuous as the promise of "sexual allure" that enveloped the products displayed at that circa 1960s car show. BTW, as I wandered deeper into the Expo Hall, the impact of my car show flashback was intensified by several flashy cars on display, tended to by provocatively costumed young women.
Next, I fast forwarded from the 1960s to the 1980s, and pondered the way in which the RSA Conference had come to resemble Comdex, and I realized, why yes, this was similar to the dilemma of information security professionals reporting within an IT organization, even if directly to the CIO, rather than to somewhere else in the organization. The priorities are skewed, the emphasis is on the wrong issues. Instead of being a vital sphere within which serious security professionals endeavor to deepen an ongoing, holistic vision, touching on myriad aspects of human culture and civilization, the information security "industry" was being driven in circles by quarterly profits, etc., just as those lowly security officers who report to the CIO are being driven in circles by Return on Investment (ROI). And I assure you that whether those security officers are placated with a C-level title or not really doesn't matter, if they report to the CIO, they are not in reality C-level executives, and therefore their voices can be shut out of the big decisions.
But do not despair. I did return from RSA 2012 with some meaningful takeaways to share with you.
Crypto Panel
On the annual Crypto Panel, Whit Diffie, Ron Rivest and Adi Shamir continued to fire flares into the night sky, briefly illuminating the dark and dangerous terrain into which we have stumbled.
Ari Juels re: "alleged RSA crypto flaw" - "Ron was wrong, Whit is right?"
Ron Rivest: "Ari is wrong, Nadia [Heninger] is right"
Adi Shamir: "Ron is wrong, Whit is right, & the NSA is happy"
Whit Diffie re: Wikileaks - "You could describe it as much of a success as a failure," it required a walk-in ...
Whit Diffie: In security you go from one failure to another, in attacking you move from one success to another."
Rivest: Internet voting is a bad idea. Low-tech is good for voting; complexity breeds insecurity, the physical ballot adds value.
Shamir re: debate about which U.S. government agency should be responsible for Internet security, the NSA or DHS - Make the people responsible for airport security responsible for Internet security? Will we take off our shoes when getting on the Internet? Let the NSA do it, let the professionals do it.
Juels: Crypto is science, but will there ever b a science of cybersecurity?
Shamir: Question should not be are we going to have theory of defense against cyber attacks, but should we?
Rivest on the future of crypto: Crypto has been moving to the edge of the cliff; the edge of the cliff is the assumption that we can keep keys secure. Crypto succeeds when it is no longer the weakest link.
Shamir on cloud computing: When things get hot, clouds disappear; be careful about uploading things to a cloud which can disappear suddenly.
Whit Diffie: David Brin's point is that either everyone is going to know everything, or only the secret police are going to know ...
Uncommon Sense about Cyber War
I highly value Marcus Ranum's perspectives on cyber security.
And his RSA 2012 talk, Cyber War: You're Doing It Wrong! The Relationship Between Four Threats in the 21st Century, did not disappoint.
Here are a few rich excerpts and three compelling slides.
"I would love to have someone tell me what the difference is between 'active defense' and offense ... Cyberspace is being metaphorized as a new battlefield. What is very interesting to me is that the actual details are getting lost in the analogy. We as computer security practitioners do not have to talk about 'cyber war' as if it is warfare; we can talk about 'cyber war' as if it were just another aspect of computer security, because we already have the vocabulary for doing that ... I want to pick apart some of the memes of this whole 'cyber war' thing, so we can eventually roll back and talk about them in terms of computer security and the properties of computer security ... "
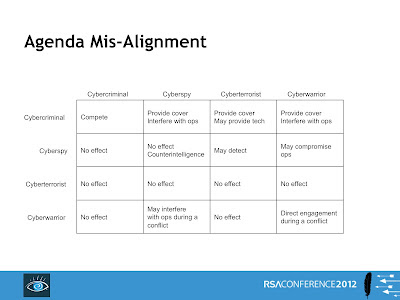
"We constantly hear from our government that the private sector has to step up and get involved in protecting itself against 'cyber war.' We have stepped up and gotten involved in protecting against 'cyber war.' We, the private sector, built that humongous room full of products across the hall, they are all cyber weapons to defend ourselves. We have done our job. It's the counterintelligence part, the managing of the geopolitical process, to prevent us from being an attractive attack target that's not being done. So the correct answer when people from the government say that you in the private sector have to step up to protect us - from Iranian attack, or from Lichenstein taking down our ATM network - is that's what we pay you $30 billion a year to do. Why don't you do your job, and let us get back to protecting our networks against the criminals, because if we protect our networks adequately against the criminals, we've probably gone a long way to protecting it against ordinary spies and ordinary cyber warriors. The strategic problems are not our problems. My strategic problem as a business man is to run and grow my business, and boost the economy; your strategic problem as a politician is to protect the nation and to avoid getting into wars foreign or domestic ... I am a cyber pacifist ... "

"Defenses overlap a whole lot. I deputize all of you. The next time someone starts talking about 'the Art of War' in cyberspace, and they say 'the best defense is a good offense,' I deputize you to smack them on the back of the head. OK? Because in cyberspace, the best defense is a good defense. It is not a physical domain, as in war. The reason the best defense is a strong offense in war is because you can launch a spoiling attack against where your enemy's troops are assembling. If I know you have 20,000 guys out there and you are planning to attack me, and I can bomb them, then I win, or at least I am able to degrade your ability to attack me. Do that apply in cyberspace? No. Because your enemy can create their own pocket of reality that is not connected to your pocket of reality, they can do all their testing, and their force assembling, in this other reality, and then they can connect to your reality any time they want, do a bunch of bad stuff to you, and then disconnect any time they want. It bears no resemblance whatsoever to the traditional properties of warfare. It is a completely different game ... The defensive approaches overlap, because anything we do to protect ourselves against one are probably going to protect us against another. So the only thing left to do is this kind of strategic analysis, to do counterintelligence, which I am not going to do, I am the CSO of a small computer security start up ... I am not going to carry out counter-intelligence against the Mossad, I am just not going to do it, I am just not tall enough, I don't have the budget ... probably IBM doesn't have the budget, actually IBM probably does have the budget, but they are not going to do that either, because their share-holders would have a great big WTF at one of their board meetings. 'Why are you guys spying on the Mossad?' 'Well, we're afraid they are going to spy on us, so we decided to have an active defense.' Gimme a break ..."

"So the [cyberwar] tools are going to have to be different unless we want to have this overlapping attack and defense problem; because if I am defending against the cybercrime tools, i.e., looking for malware and botnets, doing my intrusion detection, got my next generation firewall, and a pair of bolt cutters attached to my network, and I have secured my network, I have also secured my network against the spies and the cyber warriors, so they are going to need a completely different application stack ... I am trying to penetrate your networks without using TCP/IP at all, that's the kind of problem we are talking about. And they actually are some techniques for doing that, but they involved some pretty complicated devices, and agents in place, and all kinds of really fancy stuff. The point here is that I want you to question the realism of the logistics of the weapons that may or may not exist. Most of what we are talking about when we are talking about offensive cyber war sounds an awful lot like malware; malware written by buddies of the guys who are writing malware for the Russian Business Network, they are just writing militarized malware, but it is still malware and it is still going to get caught by my intrusion detection system if I am the kind of crazy person who looks at everything ..."
Related Posts
RSA 2011: One Flew Over the Kaku's Nest & Other Ruminations
RSA 2010: Lost in the Cloud, & Shrouded in the Fog of War, How Far Into the Cyber Future Can You Peer? Can You See Even Beyond Your Next Step?
RSA Conference 2009: Summary of Posts
Subscribe to:
Posts (Atom)
